
 |
 |
 |
 |

|
|
||||
LynxOS Networking Guide |
|||||
net-SNMP and OpenSSL
Introduction
net-SNMP (previously known as UCD-SNMP) is an implementation of the SNMP (Simple Network Management Protocol) protocol.
SNMP is used to deliver network management information between networked hosts. Administrators can manage certain aspects of networking using net-SNMP, including performance management and problem detection. net-SNMP is comprised of various tools related to SNMP management, including:
- An extensible Agent
- An SNMP library
- Tools to request or set information from SNMP Agents
- Tools to generate and handle SNMP traps
- A version of the UNIX netstat command, using SNMP
- A Tk/perl MIB browser
LynxOS includes net-SNMP version 4.1.1 which supports SNMPv2 and SNMPv3 (see following note), and MIBI and MIBII.
Use of OpenSSL outside of SNMPv3 is unsupported. Refer to "OpenSSL Legal Issues" for additional legal restrictions.
net-SNMP sends and receives information through UDP ports 161 (SNMP) and 162 (SNMP Traps).
Installing net-SNMP
net-SNMP components are installed during the initial LynxOS installation. To enable net-SNMP functionality, users must run the Install.snmp script to update the /net/rc.network file. net-SNMP can be disabled with the Uninstall.snmp script.
Run the Install script to enable snmp functionality:
The Install.snmp and Uninstall.snmp scripts are found in the /usr/bin/ directory.
SNMP Overview
SNMP architecture is comprised of three elements: Managed Devices, Agents, and Network Management Stations (NMS).
Managed devices can be any device node on a network, including PCs, Hubs, Routers, and Printers. Agents are software modules that are responsible for maintaining information on a specific device node. Agents collect and store information about a particular device in a local management database, for use by network management stations. The Network Management Station (NMS) provides a user interface to applications and network information. Network management stations collect information from Agents for the Management Information Base (MIB), and can set the types of data the Agents report. The MIB is a hierarchical database of all managed devices on a network managed by SNMP.
The following figure shows the communication between managed devices, Agents, and the network management station.
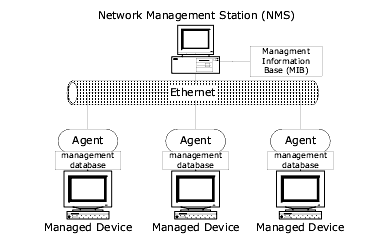
SNMP Basic ArchitectureIn this example, Agents act as an interface between the network management station and the managed devices on the network. Each Agent resides on the device as a software module and provides information to the NMS. The NMS maintains the Management Information Base (MIB), a hierarchical table of all entities on the network.
net-SNMP Documentation
Included with the net-SNMP distribution for LynxOS are several documents, including:
Additional resources and documentation are also available online at:
net-SNMP Components
The following tables describe the net-SNMP daemons and applications included with the LynxOS distribution. Each of the following components is described in its respective man page.
Configuring SNMPv3
Use the following instructions to set up users for SNMPv3.
Creating a User
To create an SNMPv3 user, follow these instructions:
- Before creating the SNMPv3 user, update the $ENV_PREFIX/usr/snmp/share/snmpconf/snmpd.conf file to provide the users access to SNMPv3. For example:
- To create the user, edit the file $ENV_PREFIX/usr/snmp/share/snmp/snmpconf/snmpd.conf and add the createUser command:
where <myuser> and <my_password> are the username and password of the user account. Passwords must be at least 8 characters long.
# cd $ENV_PREFIX/usr/snmp/sbin/snmpd
# snmpget -v 3 -u myuser -l authNoPriv \
-a MD5 -A my_password localhost sysUpTime.0
By placing the createUser line in snmpd.conf, the password is automatically erased from the file the next time the agent shuts down. This way, only the derived secret key are remembered. Also, only the localized secret key is remembered and if the machine is broken into, it is impossible to use this localized key to get access to any of your other hosts.
Creating Additional Users
Once the first user is created, additional users can be created from the command line. The snmpusm command appends the new user information to snmp.conf so the new user can be accessed when SNMP starts.
Use the following instructions to add additional users.
- Before starting the SNMP agent, edit the /usr/snmp/share/snmp/snmpconf/snmpd.conf file to add the name of the new user. For example,
Where <newuser> is the name of the new user to create. A new user is created with the same password as the myuser account. To change the password, type the following command:
# snmpusm -v 3 -u newuser -l authNoPriv \
-a MD5 -A my_password localhost passwd \
-CO my_password -CN <newpassword>
Extending the Agent with MIB modules
Custom modules can be added to extend the functionality of Agents. Refer to the documentation on AgentX, SMUX and proxied SNMP included with the net-SNMP distribution for more details. All three mechanisms use the same module API, which is described in the AGENT.txt file, included with the distribution. There is also an HTML version accessible from the net-SNMP project web page (http://net-snmp.sourceforge.net).
The mib2c tool can be used to facilitate writing MIB modules. mib2c generates most of the necessary skeleton code from the description in the MIB file. Note that the net-SNMP suite does not currently include support for SMUX subagents.
License & Copyright
net-SNMP is free software distributed under the GNU General Public License (GPL). Other Documents and product updates related to net-SNMP are available from: http://net-snmp.sourceforge.net. Some of the documentation in this guide is taken from the net-SNMP FAQ, man pages, and Readme files. In some cases, content has changed for LynxOS specific environments. Unmodified versions of these documents can be found on the net-SNMP homepage.
Copyright 1989, 1991, 1992 by Carnegie Mellon University Derivative Work
Copyright 1996, 1998, 1999, 2000 The Regents of the University of California All Rights Reserved Permission to use, copy, modify and distribute this software and its documentation for any purpose and without fee is hereby granted, provided that the above copyright notice appears in all copies and that both that copyright notice and this permission notice appear in supporting documentation, and that the name of CMU and The Regents of the University of California not be used in advertising or publicity pertaining to distribution of the software without specific written permission.
CMU AND THE REGENTS OF THE UNIVERSITY OF CALIFORNIA DISCLAIM ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL CMU OR THE REGENTS OF THE UNIVERSITY OF CALIFORNIA BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM THE LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
OpenSSL
The SHA authentication and DES encryption components of SNMPv3 require the OpenSSL package, which is provided as a tarball on a separate CD-ROM in the LynxOS package. Please be aware that this version of OpenSSL is an unmodified version of the open-source distribution built on LynxOS and is provided for the SNMPv3 encryptionfunctionality only. Use of OpenSSL outside of SNMPv3 is unsupported.
Refer to the LynxOS Installation Guide for instructions on installing OpenSSL.
OpenSSL Legal Issues
The OpenSSL package (required for certain SNMPv3 components) uses strong cryptography, which may fall under certain import/export restrictions in certain countries. Use of strong cryptography, use of cryptography hooks, or communicating technical details about cryptography software is illegal in some countries. Please be aware of any import/export and/or use laws which apply.
 LynuxWorks, Inc. 855 Branham Lane East San Jose, CA 95138 http://www.lynuxworks.com 1.800.255.5969 |
 |
 |
 |
 |